Securing Corporate Data in the Age of Rising Global Cyber Threats
In today’s interconnected world, cybersecurity has become a critical concern for businesses of all sizes. The rapid evolution of cyber threats and the increasing sophistication of attackers have made securing corporate data more important than ever. The recent CrowdStrike outage, which disrupted global computer systems, highlighted the critical role of cybersecurity solutions in modern IT infrastructure. Although the outage itself was not the result of a cyber attack, it underscored the widespread reliance on security products across numerous organizations worldwide.
This article explores the various dimensions of cybersecurity, the importance of protecting data in a cloud-based environment, and the role of AI in both enhancing and combating cyber threats. At AMI, we view cybersecurity as a compelling long-term investment theme due to the persistent and increasingly sophisticated nature of cyber threats. Moreover, the shift from hardware to software solutions within the cybersecurity sector has transformed revenue models, making these companies’ revenue streams more predictable and recurring compared to historical hardware-centric models.
The Escalating Threat Landscape
The digital age has brought remarkable advancements, but it has also opened the door to a surge in cyber threats. Cybercriminals are employing increasingly sophisticated methods to exploit vulnerabilities and access sensitive information. Common threats include:
- Ransomware Attacks: These attacks involve encrypting a victim’s data and demanding a ransom for its release. Recent high-profile ransomware incidents have demonstrated the devastating impact on businesses, including operational disruptions and financial losses.
- Phishing Schemes: Phishing attacks involve tricking individuals into revealing confidential information, such as login credentials, through deceptive emails or websites. These attacks can lead to unauthorized access to corporate systems.
- Malware: Malicious software designed to damage or gain unauthorized access to systems. Malware can come in various forms, including viruses, trojans, and spyware.
Recent Large-Scale Threats and Their Impact
The growing prevalence of large-scale cyber threats underscores the need for advanced security solutions. These threats are not going away and are getting increasingly more sophisticated. Some notable examples include:
- The Colonial Pipeline Ransomware Attack: In 2021, a ransomware attack on Colonial Pipeline led to significant fuel shortages across the Eastern United States, highlighting the potential for operational disruptions caused by cyber threats.
- The SolarWinds Cyberattack: This sophisticated supply chain attack, discovered in 2020, compromised numerous high-profile organizations by exploiting vulnerabilities in the SolarWinds software.
Other notable attacks include data breaches at Equifax, Capital One, and Target which exposed financial data and other personal financial information for hundreds of millions of individuals. These incidents reflect a trend where cyber threats are not only persistent but increasingly sophisticated. Attackers are no longer just individual hackers operating from their basements; they include highly organized state-sponsored actors from nations such as Russia, Iran, and North Korea. These state actors have the resources and expertise to carry out complex and destructive attacks, making the cybersecurity landscape even more challenging. The evolving nature of these threats, driven by both advanced technology and geopolitical motivations, means that the need for robust, cutting-edge security measures is greater than ever.
These attacks come at a great cost:
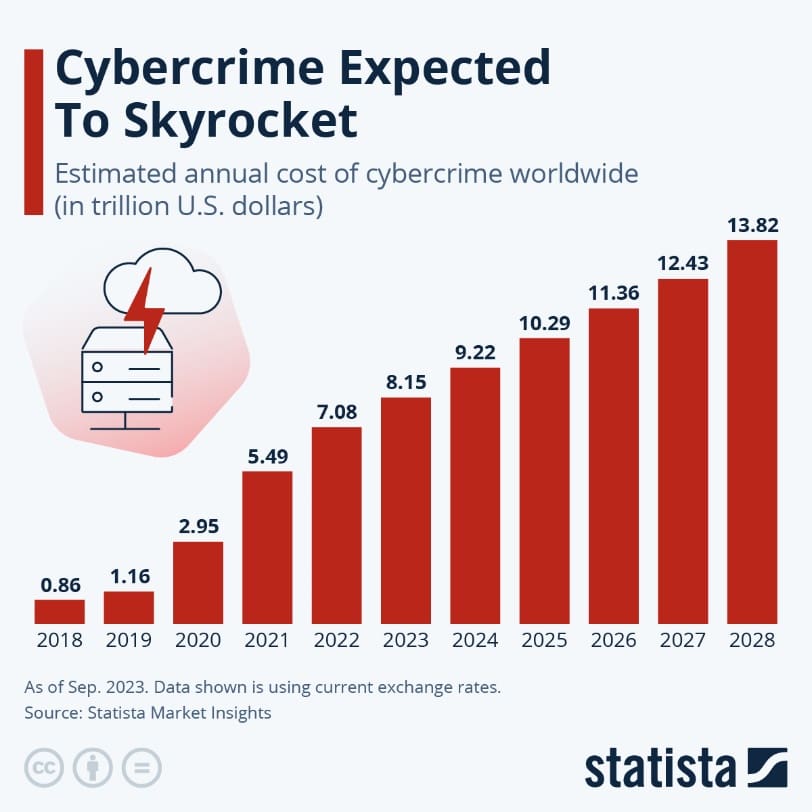
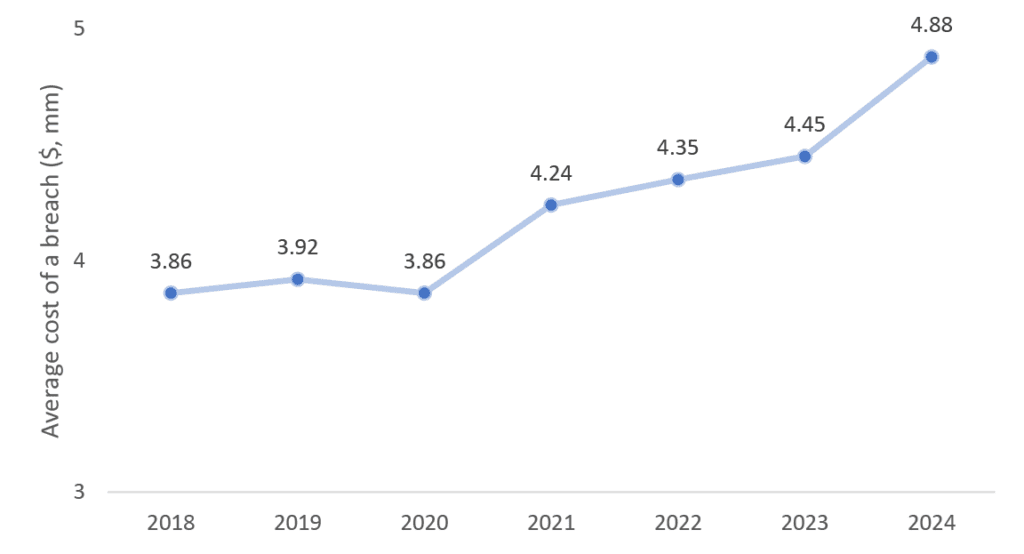
Source: JP Morgan, IBM Cost of a Data Breach Report, July 2024
How Enterprises Guard Their Corporate Data
To counter these costly threats, businesses must implement robust cybersecurity measures. Here are key strategies for protecting corporate data:
1. Comprehensive Security Frameworks: Establishing a multi-layered security framework is crucial. This includes firewalls, intrusion detection systems, and endpoint protection solutions to create a fortified defense against potential breaches.
2. Regular Security Assessments: Conducting regular vulnerability assessments and penetration testing helps identify and address security weaknesses before they can be exploited by attackers.
3. Employee Training: Human error remains a significant vulnerability. Regular training programs to educate employees about recognizing phishing attempts and adhering to security best practices can significantly reduce the risk of breaches.
4. Incident Response Plans: Having a well-defined incident response plan ensures that organizations can quickly and effectively respond to security breaches, minimizing damage and recovery time.
How Enterprises Guard Their Corporate Data
To counter these costly threats, businesses must implement robust cybersecurity measures. Here are key strategies for protecting corporate data:
1. Comprehensive Security Frameworks: Establishing a multi-layered security framework is crucial. This includes firewalls, intrusion detection systems, and endpoint protection solutions to create a fortified defense against potential breaches.
2. Regular Security Assessments: Conducting regular vulnerability assessments and penetration testing helps identify and address security weaknesses before they can be exploited by attackers.
3. Employee Training: Human error remains a significant vulnerability. Regular training programs to educate employees about recognizing phishing attempts and adhering to security best practices can significantly reduce the risk of breaches.
4. Incident Response Plans: Having a well-defined incident response plan ensures that organizations can quickly and effectively respond to security breaches, minimizing damage and recovery time.
The shift to cloud computing has revolutionized business operations by providing flexibility and scalability, but it also brings new security challenges. Safeguarding data in a cloud-based environment necessitates robust measures, including encryption of data both at rest and in transit to prevent unauthorized access, stringent access controls and identity management to ensure only authorized personnel can access sensitive information, and specialized cloud security tools to monitor and protect against threats like misconfigurations and unauthorized access. Additionally, Secure Access Service Edge (SASE) is emerging as a critical component in this landscape. SASE integrates network security functions, such as secure web gateways and firewall-as-a-service, with wide-area network (WAN) capabilities into a unified, cloud-delivered service. This comprehensive approach enhances security and performance by streamlining network and security functions into a single solution, which is particularly valuable in an era of remote work and cloud computing.
The Role of AI in Cybersecurity
Artificial Intelligence (AI) has become a transformative force in cybersecurity, playing a dual role in both enhancing security measures and facilitating cyber threats.
AI has revolutionized the ability to detect and respond to cyber threats. Here’s how:
- Behavioral Analysis: AI algorithms can analyze user behavior and network traffic to identify anomalies that may indicate a cyber threat. For example, unusual login patterns or unexpected data transfers can be flagged for further investigation.
- Threat Intelligence: AI can process vast amounts of data from various sources to provide real-time threat intelligence. This helps in identifying emerging threats and vulnerabilities, enabling organizations to respond proactively.
- Automated Response: AI-powered systems can automatically respond to detected threats by isolating affected systems, blocking malicious traffic, or applying patches, thereby reducing the time between detection and remediation.
Extensive use of AI in security can help reduce the number of days to identify and contain a breach:
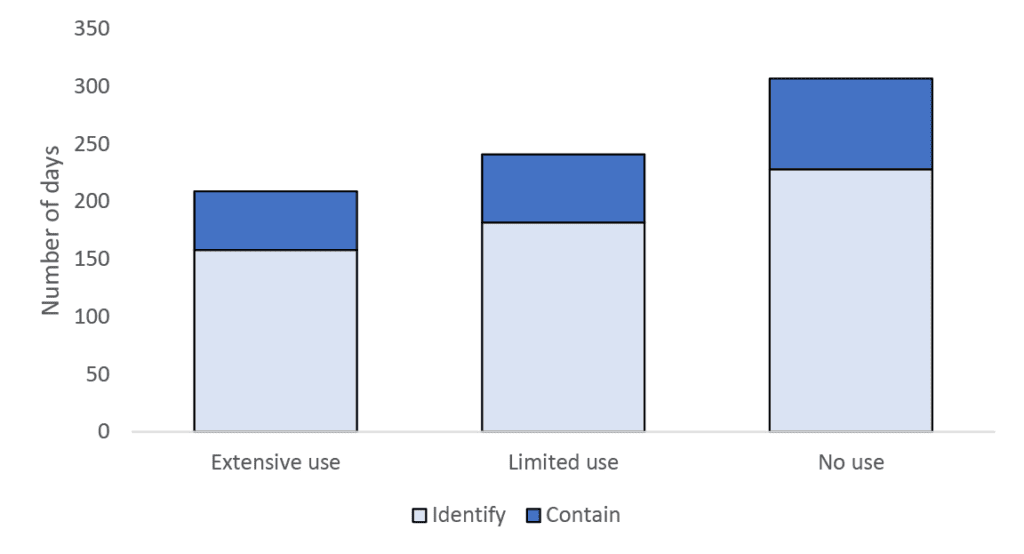
Source: JP Morgan, IBM Cost of a Data Breach Report, July 2024
Unfortunately, AI is also being used by cybercriminals to enhance their attack capabilities:
- Sophisticated Phishing: AI can craft highly convincing phishing emails by analyzing personal data and mimicking writing styles. This increases the likelihood of tricking individuals into divulging sensitive information.
- Adaptive Malware: AI-driven malware can adapt and evolve to evade traditional security measures. It can modify its behavior based on the environment, making it more difficult to detect and combat.
Automated Attacks: AI can automate various stages of a cyber attack, from scanning for vulnerabilities to executing attacks at scale. This increases the efficiency and effectiveness of malicious campaigns.
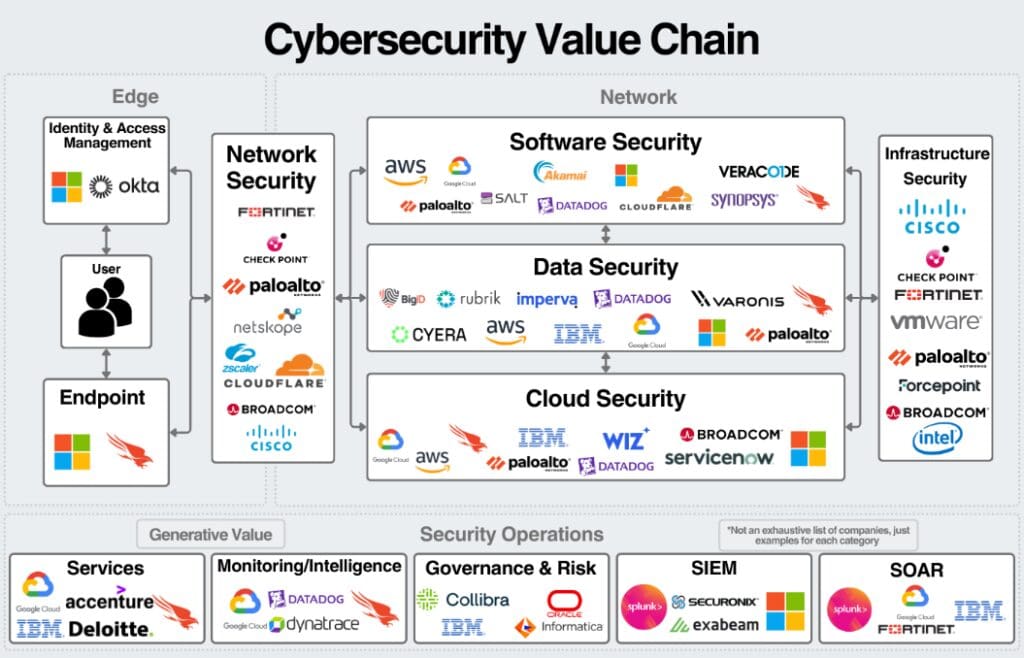
Key Players in Cybersecurity
To combat these threats, several companies are leading the charge in cybersecurity. Their solutions are crucial for protecting enterprises against a wide range of cyber risks:
- Palo Alto Networks (PANW): Known for its next-generation firewalls and comprehensive threat intelligence, Palo Alto Networks provides a range of solutions to safeguard enterprise networks and data. Palo Alto is an AMI Large Cap Growth holding. We like the company’s recent efforts to offer customers a full suite of cyber security solutions on a single platform, which should improve retention and allow for more opportunities to grow.
- Fortinet (FTNT): Offering integrated security solutions, Fortinet is renowned for its robust firewalls and advanced threat protection capabilities, helping businesses defend against a variety of cyber threats.
- CyberArk (CYBR): Specializing in privileged access management, CyberArk helps organizations secure and manage access to critical systems and sensitive information, reducing the risk of insider threats and unauthorized access. CyberArk is an AMI Small Cap Growth holding. As a leader in identity management, we like the company’s high level of subscription revenue which has proven to be very durable in recent quarters.
- CrowdStrike (CRWD): With its focus on endpoint protection, CrowdStrike provides advanced threat detection and response solutions to safeguard against sophisticated attacks targeting endpoints.
- Microsoft (MSFT): Microsoft provides a robust cybersecurity framework through solutions such as Microsoft Defender for comprehensive endpoint and cloud security, Azure Security Center for unified security management across cloud and on-premises environments, and Microsoft Sentinel for advanced threat detection and response. Their integrated approach leverages AI and cloud technologies to offer extensive protection and management across enterprise IT ecosystems. Microsoft is an AMI Large Cap Growth holding. We are attracted to this investment in Microsoft due to the company’s diversified business model, which encompasses not only cybersecurity but also software and services that support cloud offerings and digital transformation projects. Additionally, Microsoft’s leadership in AI, demonstrated through its investment in OpenAI and the development of its ‘Copilot’ AI, further enhances its appeal.
- Splunk (CSCO): Recently acquired by Cisco, Splunk is known for its security information and event management (SIEM) solutions, Splunk helps organizations analyze and respond to security events in real time, enhancing overall threat detection and response capabilities.
- Tenable (TENB): Specializing in vulnerability management, Tenable’s Nessus and Tenable.io solutions provide extensive vulnerability scanning and assessment capabilities, helping organizations identify and remediate security weaknesses. Tenable is an AMI Small Cap Growth holding. We like Tenable for its leadership in vulnerability management—a critical component within cybersecurity—as well as its recent AI-enabled products, such as Tenable One, which enhance its offerings with advanced threat detection capabilities.
- Broadcom (AVGO): Through its acquisition of Symantec’s Enterprise Security business, Broadcom has become a significant player in cybersecurity, providing solutions including endpoint protection, data loss prevention, and vulnerability management with the Symantec Enterprise Security suite. Additionally, Broadcom recently acquired VMware, further expanding its reach into cloud infrastructure and management, which complements its cybersecurity offerings by integrating with VMware’s virtualization and cloud solutions. Broadcom is an AMI Large Cap Growth holding. We appreciate Broadcom’s recent expansion into software, which introduces a more recurring revenue component and also provides us with exposure to data center infrastructure.
Investment Opportunities in Cybersecurity
Given the rising threat landscape, increasing sophistication of attacks, and the ever-growing value of data, the demand for advanced cybersecurity solutions is on a secular uptrend. This creates a compelling investment opportunity in the cybersecurity sector. Here’s why:
- Secular Tailwind: The cybersecurity industry benefits from a long-term growth trend driven by the escalating frequency and sophistication of cyber threats. As more businesses and individuals move online, the need for robust security measures grows, creating a steady demand for cybersecurity solutions.
- Increased Complexity and Value of Data: With data becoming an increasingly valuable asset, protecting it has become a top priority for organizations. This heightened focus on data security fuels investments in advanced cybersecurity technologies and services.
- Innovation and Differentiation: Leading companies in cybersecurity are continually innovating, developing cutting-edge solutions that address emerging threats. Investing in these companies offers exposure to technological advancements and the potential for substantial returns as they drive growth in the industry.
- High Barriers to Entry: The complexity of cybersecurity solutions and the need for ongoing research and development create high barriers to entry for new competitors. Established players with strong reputations and advanced technologies are well-positioned to capitalize on the growing market.
According to the 2024 Voice of the CISO report by ProofPoint, 70% of Chief Information Security Officers (CISOs) believe they are at risk of experiencing a significant cyber attack within the next year. Additionally, during CyberArk’s Q2 2024 earnings call, CEO Matt Cohen reported that “last year, 93% of organizations fell victim to an identity-related cyber attack, and nearly all of them experienced multiple incidents.“
Conclusion
As cyber threats continue to evolve and grow in sophistication, the importance of robust cybersecurity measures cannot be overstated. Businesses must remain vigilant and proactive in safeguarding their corporate data, particularly in a cloud-based environment. By leveraging advanced security solutions from leading companies and adopting a comprehensive approach to cybersecurity, enterprises can better protect themselves against the ever-present and evolving cyber threat landscape. We believe these companies will see robust demand for many years and thus have made them an important component within AMI’s strategies.
Disclosure
This communication is prepared and distributed by AMI Asset Management (AMI), an SEC-registered investment adviser (registration does not imply a certain level of skill or training). The information contained herein, and the opinions expressed are those of AMI as of the date of writing, prepared solely for general informational and discussion purposes. The information contained in this communication has been compiled by AMI from sources believed to be reliable; however, AMI does not make any representation as to their accuracy, completeness or correctness and does not accept liability for any loss arising from the use hereof. Such information and opinions are subject to change without notice due to changes in market or economic conditions and may not necessarily come to pass. References to specific securities are not intended as recommendations of said securities. The reader should not assume that any investments in securities, sectors and markets identified or described were or will be profitable. Investing entails risks, including possible loss of principal. Past performance is not a guide to future performance and future returns are not guaranteed. The investment strategies referenced may not be suitable or appropriate for all investors depending on their specific investment objectives and financial situation and potential investors should consult with their own financial professional before determining whether to invest in the strategy.
FOR FINANCIAL PROFESSIONAL USE ONLY. NOT TO BE SHOWN OR DISTRIBUTED TO THE PUBLC.
